X, formerly known as Twitter, has launched its new end-to-end encrypted chat feature, but cybersecurity experts are sounding alarm bells about critical security vulnerabilities that make the platform potentially dangerous for private communications.
X’s End-to-End Encrypted Chat Implementation Raises Red Flags
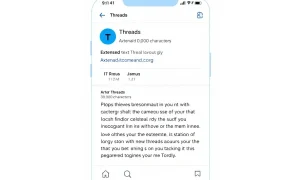
X recently began rolling out its encrypted messaging service called XChat. The company claims this new feature provides true end-to-end encryption. However, security researchers immediately identified multiple concerning issues with the implementation.
Critical Security Flaws in XChat’s Encryption
Matthew Garrett, a prominent security researcher, published detailed analysis showing several fundamental problems with X’s approach to end-to-end encrypted chat:
- Private key storage on X servers instead of user devices
- Four-digit PIN protection for cryptographic keys
- No hardware security module verification provided
- Potential adversary-in-the-middle attacks possible
How X’s End-to-End Encrypted Chat Differs From Signal
Unlike Signal, which sets the gold standard for end-to-end encrypted chat, X’s implementation lacks several critical security features. Signal stores private keys locally on user devices and uses robust cryptographic protocols. Conversely, X stores keys on its servers protected only by weak four-digit PINs.
Open Source Transparency Missing From XChat
Another major concern involves XChat’s closed-source nature. Signal’s entire codebase is open for public scrutiny, allowing independent verification of security claims. X promises to open source its implementation later this year but currently operates without third-party validation.
Perfect Forward Secrecy Absent From Platform
X admits its end-to-end encrypted chat lacks perfect forward secrecy. This cryptographic feature ensures compromised keys only affect individual messages rather than entire conversation histories. The absence of this protection represents a significant security shortfall.
Expert Recommendations Regarding X’s Encrypted Chat
Cryptography experts uniformly advise against trusting X’s end-to-end encrypted chat for sensitive communications. Matthew Green from Johns Hopkins University stated he wouldn’t trust it more than unencrypted direct messages without independent security audits.
Frequently Asked Questions
What is end-to-end encryption?
End-to-end encryption ensures only communicating users can read messages, preventing third parties including service providers from accessing content.
How does X’s encryption differ from Signal?
Signal stores encryption keys on user devices while X stores them on company servers protected by weak four-digit PINs.
Should I use XChat for sensitive conversations?
Security experts strongly recommend against using XChat for any sensitive communications until independent audits verify its security.
When will X open source its encryption implementation?
X states it plans to open source the technology and publish a technical whitepaper later this year, but no specific timeline exists.
What are the biggest security concerns with XChat?
Key concerns include server-side key storage, weak PIN protection, lack of perfect forward secrecy, and potential adversary-in-the-middle attacks.
Has X provided proof of using hardware security modules?
An X engineer claimed HSMs are used but provided no verifiable evidence, leaving security researchers skeptical about actual implementation.